A vulnerability in the popular Rust crate async-tar has affected the fast uv Python package manager, which uses a forked version that’s now patched – but the most widely downloaded version remains unfixed.
The vulnerability is an error in the header parsing code that allows an attacker to hide additional files in a tar archive, discovered by a team at secure computing company Edera.
The tar format can support both ustar (Unix Standard TAR) and pax headers, the latter was added as an extension to tar decades ago. When a file entry has both ustar and pax headers, the code advances the stream position based on the ustar size, often zero, rather than the pax size, which should override it. This means it may interpret file content as a tar header, enabling smuggled files. Edera stated that this enables file overwriting attacks, supply chain attacks “via build system and package manager exploitation,” and bypass of BOM (bill of materials) security scanning.
The normal disclosure pattern for a vulnerability is that maintainers are informed in advance to create patches before the issue is widely known. In this case, though, there are several important forks of async-tar. The version used by uv is astral-tokio-tar, which, the readme states, “is a fork of edera-dev/tokio-tar, which was a fork of vorot93/tokio-tar, which was a fork of dignifiedquire/async-tar, which is based on alexcrichton/tar-rs.”
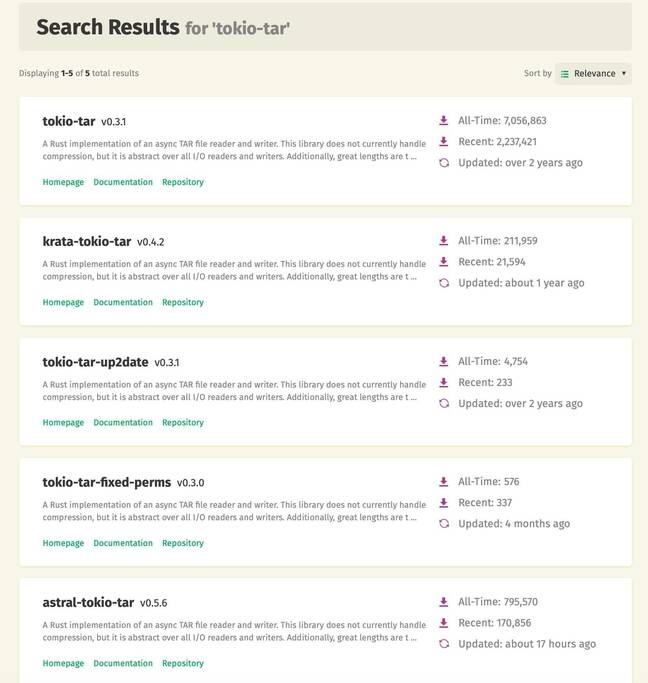
The most popular tokio-tar crate has not been fixed, and the only fixed version in this list is shown last
The fork called tokio-tar is the most popular, according to crates.io, with over 7 million downloads, but the Edera team had problems contacting the maintainers of both tokio-tar and async-tar, because “neither project had a SECURITY.md or public contact method,” resorting to what it called social engineering and community sleuthing to find the right people. The outcome is that while both async-tar and astral-tokio-tar have been patched, tokio-tar has not. Edera said that it “appears to be abandonware” and recommends switching to one of the patched forks, or to the standard tar crate, which is not async but works correctly.
Edera has its own fork of tokio-tar, called krata-tokio-tar, though it reported that its own products using the vulnerable version were not at risk because of other mitigations. A patch is available for Edera’s crate, but it will also now be archived in favor of Astral’s version – though at the time of writing it is still listed on crates.io.
Edera also noted that the fact software is written in Rust is no guarantee of its safety, since it protects against memory issues like buffer overflows and use-after-free, but does nothing to prevent logic errors. ®
