There is a live cross-site scripting (XSS) vulnerability in takedowns website DMCA-dot-com’s user interface. It’s existed for more than a year and the site’s operators don’t appear to be interested in fixing it.
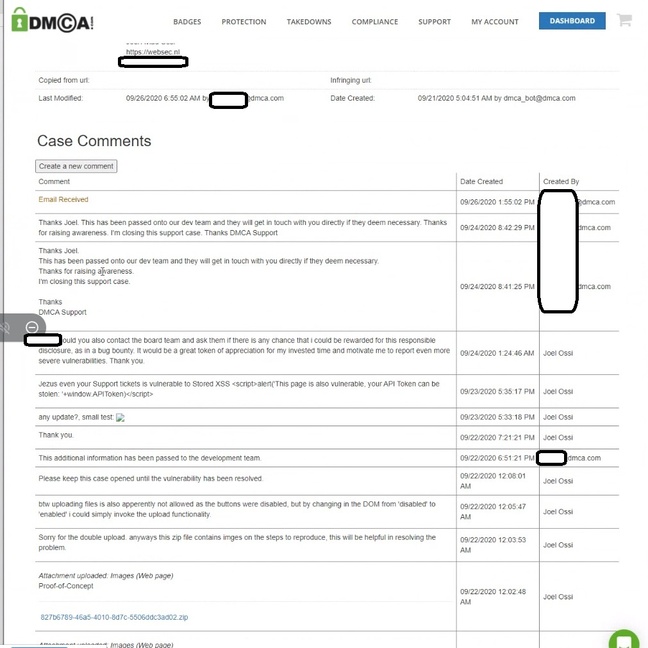
Infosec researcher Joel Ossi, founder of Dutch security firm Websec, announced his findings after spending more than a year trying and failing to get DMCA-dot-com to take the XSS seriously.
“I registered at DMCA at first with an intention to protect my own website,” he blogged, explaining that he found unescaped free-text entry boxes in the DMCA user interface allowed him to create an XSS.
DMCA-dot-com is a copyright takedown service. Users pay the site to handle the tedious part of getting an alleged copyright infringer to delete content from the World Wide Web, using the infamous US Digital Millennium Copyright Act. Prices can be as high as $199 for a takedown.
Ossi showed The Register his live findings on a video call. Every single time he clicked to a new webpage in the DMCA-dot-com user area, the classic XSS tell-tale – a popup with a custom message – appeared. The script to do so was really quite simple:
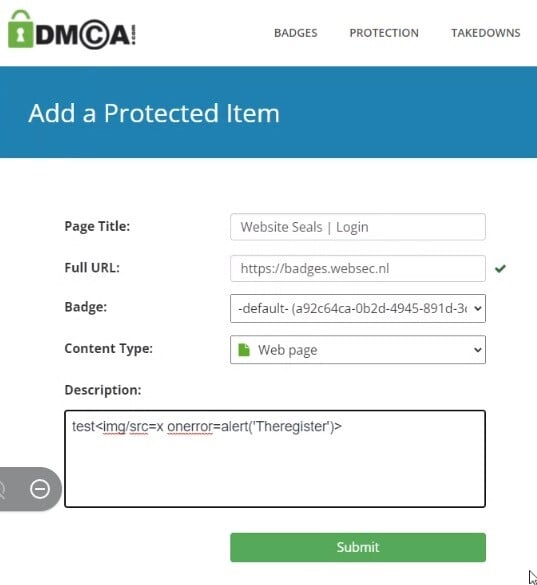
The code needed to invoke a simple XSS on DMCA-dot-com
He went public with his findings after a year spent trying and failing to get the interest of DMCA-dot-com’s operators when he first found the vuln in late 2020.
“Our development team will be reaching out if / when they need to. Our support department cannot help you on this,” said the last message sent to Ossi by DMCA-dot-com as he tried to get uninterested helpdesk folk to pass along his vuln report.
While he asked for a bug bounty, El Reg confirmed that Ossi had made full private disclosure of his findings before raising the question of payment.
Both Ossi and The Register made multiple attempts to contact DMCA-dot-com. In our case the company didn’t even acknowledge our efforts to get in touch.
While he may have been the first, Ossi isn’t the only researcher to find the XSS vulns in DMCA-dot-com. Two separate entries on the Open Bug Bounty site show XSS vulns in DMCA, one dating from April last year and the other from June.
As Reg readers know, cross-site scripting vulnerabilities let a malicious person execute scripts on somebody else’s website. As explained by MITRE, the flaw typically exists because free text entry forms don’t sanitise user inputs.
“The most common attack performed with cross-site scripting involves the disclosure of information stored in user cookies,” says MITRE. “Typically, a malicious user will craft a client-side script, which – when parsed by a web browser – perform, some activity (such as sending all site cookies to a given E-mail address).”
Harvesting active login tokens from cookies could give an attacker access to your account on DMCA-dot-com. Ossi told us it wouldn’t take much to falsely run up billable services, remove DMCA-dot-com’s protection features from a given webpage or close an account.
Jake Moore, global cybersecurity advisor to infosec firm ESET, told The Register: “Cross-site scripting vulnerabilities can allow an attacker to masquerade as a standard user and carry out any actions that the user is able to perform such as access the user’s data. User accounts can then ultimately be compromised and credentials or other information could be stolen with great ease.”
Immersive Labs’ app security specialist Sean Wright added: “Despite the fact they have been a part of the attacker toolkit for some time, many still underestimate the risks from XSS vulnerabilities. However, they are effectively client side remote code execution vulnerabilities. In the right circumstances, and combined with tools such as the Browser Exploitation Framework, XSS vulnerabilities give an attacker almost complete control of a browser. Ultimately, this could lead to redirects to malicious sites and even performing actions on behalf of the user.”
It is to be hoped that someone responsible at DMCA-dot-com pays attention to this year-and-a-half-old vuln disclosure. If it’s been around this long, somebody might be using it to do something bad. ®