Authored by SangRyol Ryu
McAfee’s Mobile Research Team discovered a software library we’ve named Goldoson, which collects lists of applications installed, and a history of Wi-Fi and Bluetooth devices information, including nearby GPS locations. Moreover, the library is armed with the functionality to perform ad fraud by clicking advertisements in the background without the user’s consent. The research team has found more than 60 applications containing this third-party malicious library, with more than 100 million downloads confirmed in the ONE store and Google Play app download markets in South Korea. While the, the risk to installers of the apps remains.
McAfee Mobile Security detects this threat as Android/Goldoson and protects customers from this and many other mobile threats. McAfee is a member of the App Defense Alliance focused on protecting users by preventing threats from reaching their devices and improving app quality across the ecosystem. We reported the discovered apps to Google, which took prompt action. reportedly notified the developers that their apps are in violation of Google Play policies and fixes are needed to reach compliance. Some apps were removed from Google Play while others were updated by the official developers. Users are encouraged to update the apps to the latest version to remove the identified threat from their devices.

Top 9 applications previously infected by Goldoson on Google Play
How does it affect users?
The Goldoson library registers the device and gets remote configurations at the same time the app runs. The library name and the remote server domain varies with each application, and it is obfuscated. The name Goldoson is after the first found domain name.
Remote configuration contains the parameters for each of functionalities and it specifies how often it runs the components. Based on the parameters, the library periodically checks, pulls device information, and sends them to the remote servers. The tags such as ‘ads_enable’ or ‘collect_enable’ indicates each functionality to work or not while other parameters define conditions and availability.
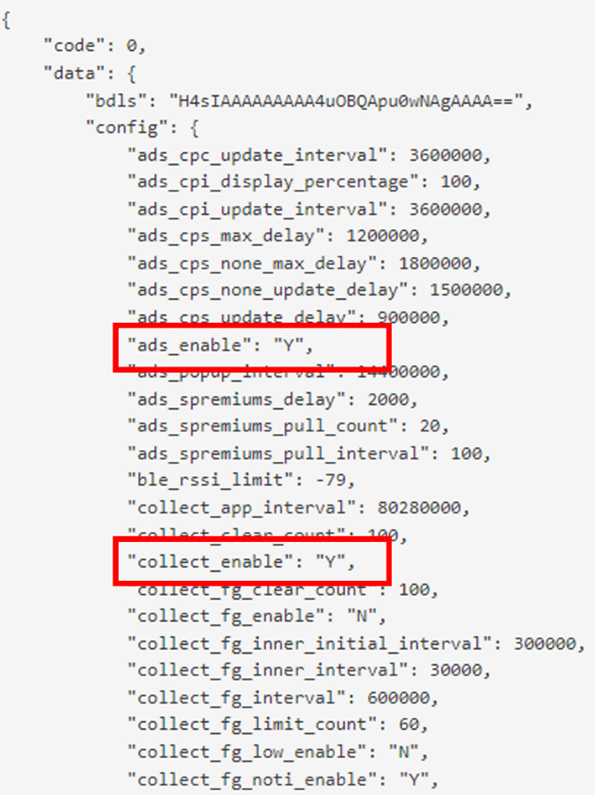
A response of remote configuration
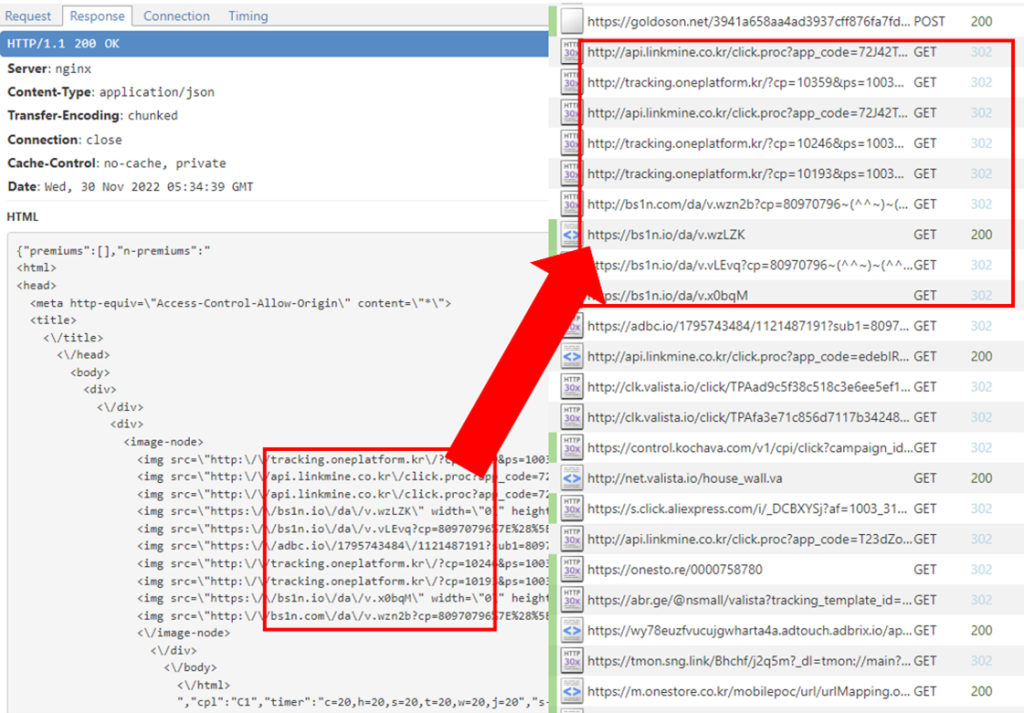
The library includes the ability to load web pages without user awareness. The functionality may be abused to load ads for financial profit. Technically, the library loads HTML code and injects it into a customized and hidden WebView and it produces hidden traffic by visiting the URLs recursively.
Collected data is sent out periodically every two days but the cycle is subject to change by the remote configuration. The information contains some sensitive data including the list of installed applications, location history, MAC address of Bluetooth and Wi-Fi nearby, and more. This may allow individuals to be identified when the data is combined. The following tables show the data observed on our test device.
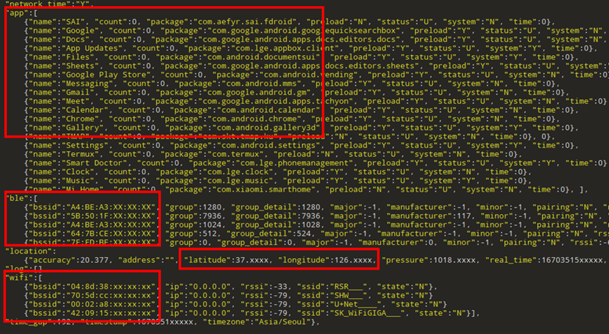
Google Play considers the list of installed apps to be personal and sensitive user data and requires a special permission declaration to get it. Users with Android 11 and above are more protected against apps attempting to gather all installed apps. However, even with the recent version of Android, we found that around 10% of the apps with Goldoson have the permission “QUERY_ALL_PACKAGES” that allows them to access app information.
Likewise, with Android 6.0 or higher, users may be asked for permissions such as Location, Storage, or Camera at runtime. If user allows the location permission, the app can access not only GPS data but also Wi-Fi and Bluetooth device information nearby. Based on BSSID (Basic Service Set Identifier) and RSSI (Received Signal Strength Indicator), the application can determine the location of the device more accurately than GPS, especially indoors.
A demo of runtime permission request
Where do the apps come from?
The infected applications come from various Android application stores. More than 100 million downloads have been tracked through Google Play. After that, ONE store, Korea’s leading app store, follows with about 8 million installations.
Conclusion
As applications continue to scale in size and leverage additional external libraries, it is important to understand their behavior. App developers should be upfront about libraries used and take precautions to protect users’ information. McAfee Mobile Security products can also help detect threats and protect you from not only malware but also unwanted programs. For more information, visit our McAfee Mobile Security.
Identified Apps and Goldoson Domains
Domains
- bhuroid.com
- enestcon.com
- htyyed.com
- discess.net
- gadlito.com
- gerfane.com
- visceun.com
- onanico.net
- methinno.net
- goldoson.net
- dalefs.com
- openwor.com
- thervide.net
- soildonutkiel.com
- treffaas.com
- sorrowdeepkold.com
- hjorsjopa.com
- dggerys.com
- ridinra.com
- necktro.com
- fuerob.com
- phyerh.net
- ojiskorp.net
- rouperdo.net
- tiffyre.net
- superdonaldkood.com
- soridok2kpop.com
List of Apps and Current Status
| Package Name | Application Name | GooglePlay Downloads | GP Status |
| com.lottemembers.android | L.POINT with L.PAY | 10M+ | Updated* |
| com.Monthly23.SwipeBrickBreaker | Swipe Brick Breaker | 10M+ | Removed** |
| com.realbyteapps.moneymanagerfree | Money Manager Expense & Budget | 10M+ | Updated* |
| com.skt.tmap.ku | TMAP – 대리,주차,전기차 충전,킥보 … | 10M+ | Updated* |
| kr.co.lottecinema.lcm | 롯데시네마 | 10M+ | Updated* |
| com.ktmusic.geniemusic | 지니뮤직 – genie | 10M+ | Updated* |
| com.cultureland.ver2 | 컬쳐랜드[컬쳐캐쉬] | 5M+ | Updated* |
| com.gretech.gomplayerko | GOM Player | 5M+ | Updated* |
| com.megabox.mop | 메가박스(Megabox) | 5M+ | Removed** |
| kr.co.psynet | LIVE Score, Real-Time Score | 5M+ | Updated* |
| sixclk.newpiki | Pikicast | 5M+ | Removed** |
| com.appsnine.compass | Compass 9: Smart Compass | 1M+ | Removed** |
| com.gomtv.gomaudio | GOM Audio – Music, Sync lyrics | 1M+ | Updated* |
| com.gretech.gomtv | 곰TV – All About Video | 1M+ | Updated* |
| com.guninnuri.guninday | 전역일 계산기 디데이 곰신톡–군인 … | 1M+ | Updated* |
| com.itemmania.imiapp | 아이템매니아 – 게임 아이템 거래 … | 1M+ | Removed** |
| com.lotteworld.android.lottemagicpass | LOTTE WORLD Magicpass | 1M+ | Updated* |
| com.Monthly23.BounceBrickBreaker | Bounce Brick Breaker | 1M+ | Removed** |
| com.Monthly23.InfiniteSlice | Infinite Slice | 1M+ | Removed** |
| com.pump.noraebang | 나홀로 노래방–쉽게 찾아 이용하는 … | 1M+ | Updated* |
| com.somcloud.somnote | SomNote – Beautiful note app | 1M+ | Removed** |
| com.whitecrow.metroid | Korea Subway Info : Metroid | 1M+ | Updated* |
| kr.co.GoodTVBible | GOODTV다번역성경찬송 | 1M+ | Removed** |
| kr.co.happymobile.happyscreen | 해피스크린 – 해피포인트를 모으 … | 1M+ | Updated* |
| kr.co.rinasoft.howuse | UBhind: Mobile Tracker Manager | 1M+ | Removed** |
| mafu.driving.free | 스피드 운전면허 필기시험 … | 1M+ | Removed** |
| com.wtwoo.girlsinger.worldcup | 이상형 월드컵 | 500K+ | Updated* |
| kr.ac.fspmobile.cu | CU편의점택배 | 500K+ | Removed** |
| com.appsnine.audiorecorder | 스마트 녹음기 : 음성 녹음기 | 100K+ | Removed** |
| com.camera.catmera | 캣메라 [순정 무음카메라] | 100K+ | Removed** |
| com.cultureland.plus | 컬쳐플러스:컬쳐랜드 혜택 더하기 … | 100K+ | Updated* |
| com.dkworks.simple_air | 창문닫아요(미세/초미세먼지/WHO … | 100K+ | Removed** |
| com.lotteworld.ticket.seoulsky | 롯데월드타워 서울스카이 | 100K+ | Updated* |
| com.Monthly23.LevelUpSnakeBall | Snake Ball Lover | 100K+ | Removed** |
| com.nmp.playgeto | 게토(geto) – PC방 게이머 필수 앱 | 100K+ | Removed** |
| com.note.app.memorymemo | 기억메모 – 심플해서 더 좋은 메모장 | 100K+ | Removed** |
| com.player.pb.stream | 풀빵 : 광고 없는 유튜브 영상 … | 100K+ | Removed** |
| com.realbyteapps.moneya | Money Manager (Remove Ads) | 100K+ | Updated* |
| com.wishpoke.fanciticon | Inssaticon – Cute Emoticons, K | 100K+ | Removed** |
| marifish.elder815.ecloud | 클라우드런처 | 100K+ | Updated* |
| com.dtryx.scinema | 작은영화관 | 50K+ | Updated* |
| com.kcld.ticketoffice | 매표소–뮤지컬문화공연 예매& … | 50K+ | Updated* |
| com.lotteworld.ticket.aquarium | 롯데월드 아쿠아리움 | 50K+ | Updated* |
| com.lotteworld.ticket.waterpark | 롯데 워터파크 | 50K+ | Updated* |
| com.skt.skaf.l001mtm091 | T map for KT, LGU+ | 50K+ | Removed** |
| org.howcompany.randomnumber | 숫자 뽑기 | 50K+ | Updated* |
| com.aog.loader | 로더(Loader) – 효과음 다운로드 앱 | 10K+ | Removed** |
| com.gomtv.gomaudio.pro | GOM Audio Plus – Music, Sync l | 10K+ | Updated* |
| com.NineGames.SwipeBrickBreaker2 | Swipe Brick Breaker 2 | 10K+ | Removed** |
| com.notice.safehome | 안심해 – 안심귀가 프로젝트 | 10K+ | Removed** |
| kr.thepay.chuncheon | 불러봄내 – 춘천시민을 위한 공공 … | 10K+ | Removed** |
| com.curation.fantaholic | 판타홀릭 – 아이돌 SNS 앱 | 5K+ | Removed** |
| com.dtryx.cinecube | 씨네큐브 | 5K+ | Updated* |
| com.p2e.tia.tnt | TNT | 5K+ | Removed** |
| com.health.bestcare | 베스트케어–위험한 전자기장, … | 1K+ | Removed** |
| com.ninegames.solitaire | InfinitySolitaire | 1K+ | Removed** |
| com.notice.newsafe | 안심해 : 안심지도 | 1K+ | Removed** |
| com.notii.cashnote | 노티아이 for 소상공인 | 1K+ | Removed** |
| com.tdi.dataone | TDI News – 최초 데이터 뉴스 앱 … | 1K+ | Removed** |
| com.ting.eyesting | 눈팅 – 여자들의 커뮤니티 | 500+ | Removed** |
| com.ting.tingsearch | 팅서치 TingSearch | 50+ | Removed** |
| com.celeb.tube.krieshachu | 츄스틱 : 크리샤츄 Fantastic | 50+ | Removed** |
| com.player.yeonhagoogokka | 연하구곡 | 10+ | Removed** |
* Updated means that the recent application on Google Play does not contain the malicious library.
** Removed means the application is not available on Google Play as of the time of posting.
