The national cybersecurity organizations of the UK and the Republic of Korea (ROK) have issued a joint advisory warning of an increased volume and sophistication of North Korean software supply chain attacks.
South Korea’s National Intelligence Service (NIS) and the UK’s National Cyber Security Centre (NCSC) said they put out the advisory to raise awareness of the serious and growing threat targeting governments, financial institutions, and defense industry companies across the world.
Zero-day and N-day vulnerabilities are being used increasingly alongside multiple exploits to achieve goals that align closely with the state “priorities” of North Korea, the pair said.
These priorities include generating funds, espionage, and the theft of intellectual property and advanced technologies from a range of industries including defense.
“In an increasingly digital and interconnected world, software supply chain attacks can have profound, far-reaching consequences for impacted organizations,” said Paul Chichester, director of operations at the NCSC.
“Today, with our partners in the Republic of Korea, we have issued a warning about the growing threat from DPRK state-linked cyber actors carrying out such attacks with increasing sophistication.
“We strongly encourage organizations to follow the mitigative actions in the advisory to improve their resilience to supply chain attacks and reduce the risk of compromise.”
The advisory is the first to be published by the NCSC jointly with another cybersecurity agency without the input of any of its equivalents from the Five Eyes intelligence alliance – the latest showing of how ties between the two nations are the closest in history.
The NCSC and NIS listed examples of zero-days and high-profile organizations exploited in attacks attributed to Lazarus, the group widely believed to be North Korea’s state-sponsored offensive cyber unit.
MagicLine4NX
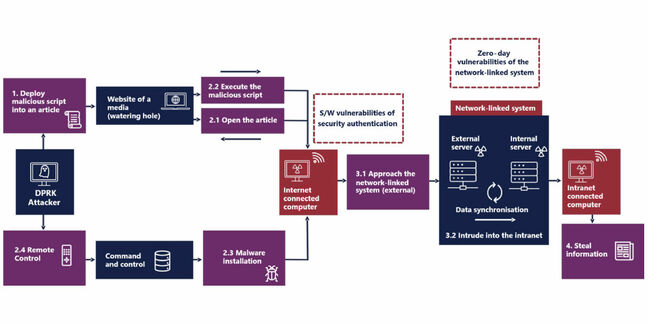
In March 2023, Lazarus attackers launched a watering hole attack to target specific groups that had vulnerable versions of the MagicLine4NX security authentication software installed.
It first compromised a media organization, poisoning a web page with malicious scripts which when visited by a user with a vulnerable MagicLine4NX installed would execute and provide attackers with remote control capabilities on the victim’s machine via C2 infrastructure.
A zero-day vulnerability was then exploited on a network-linked system via the compromised PC to breach a victim organization’s intranet – all with a view to stealing that organization’s data.
“The malicious actors used highly sophisticated modus operandi by exploiting an undisclosed vulnerability of the network-linked system and a legitimate function for intrusion into the intranet,” the advisory read.
Ultimately, security policies blocked key activity attempted by the attackers, preventing a large-scale data theft incident.
The attack itself was built on an earlier watering hole attack launched by Lazarus, then targeting the INISAFE web client with the methods used remaining unchanged in the follow-on MagicLine attacks.
Despite it not achieving the success North Korea would have wanted, the incident still provides evidence of Kim Jong Un’s ambition to target software supply chains with sophisticated methods.
3CX
The more widely publicized supply chain attack coming out of North Korea this year was that of 3CX’s desktop app, one which was slowly attributed to Lazarus as time went on and more evidence was gathered in the weeks following its March disclosure.
The incident affected high-profile targets including two critical infrastructure organizations and financial trading companies. It led the company to advise customers to use its web app instead, steering clear of the desktop software until a fix was available.
Adding to the theme of sophistication, the attack itself impacted both Windows and macOS versions of the 3CX application. Lazarus breached the company and then injected malicious code into its installer which was downloaded by users through legitimate channels.
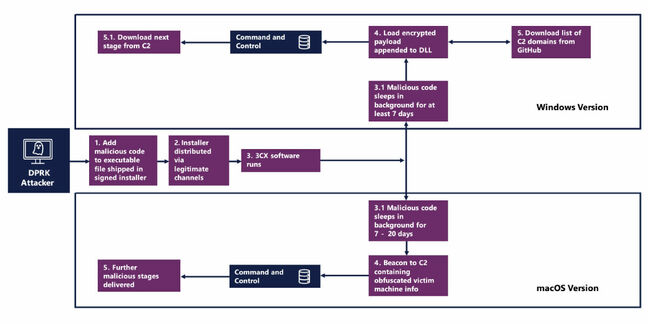
Diagram of the 3CX attack chains on Windows and macOS, courtesy of the NCSC and NIS – Click to enlarge
The infection chain was similar in both the Windows and Mac versions. Both applications installed as they normally would if they hadn’t been tampered with, and once installed they entered a sleep phase – seven days for Windows and between seven and 20 days on Mac – before transmitting data to the attackers.
The Windows malware was more capable but neither version was massively impactful. Windows attacks led to browser stealers installed, with basic system data, 3CX account information, and browser histories from Brave, Chrome, Edge, and Firefox sent back to Lazarus. For Mac users, only 3CX account information was stolen.
“The negative impact was limited because the malicious update was quickly detected by endpoint detection and response solutions,” the advisory read.
A range of suggested mitigations were suggested to follow, including enabling 2FA, applying security updates, and monitoring networks for anomalous traffic.
Microsoft weighs in
The warning comes a day after Microsoft published its own report on yet another North Korean supply chain attack, this time on CyberLink’s multimedia software.
In a similar style to the attack on 3CX, Lazarus breached the Taiwanese tech company and tampered with its installer as recently as October 20.
The malicious installer has been executed on more than 100 devices across various territories, including the US, Canada, Japan, and Taiwan, Microsoft said.
While running, the software scans the victim’s system for evidence of CrowdStrike Falcon, FireEye, or Tanium EDR security solutions. If they are found to be running, malicious activity stops dead and the software runs as normal.
If the victim isn’t running any of the three security products, then software attempts to download the second-stage payload embedded within a fake header of a PNG file, launching it in memory.
That payload then attempts to contact two URLs, both of which are illegitimate but have been previously compromised by the group.
Microsoft said it hasn’t observed hands-on-keyboard activity as a result of this supply chain attack, but it pointed to the same typical motivations of the Lazarus group that the NCSC and NIS did, indicating its potential end-goals. ®