HP’s cybersecurity folks have uncovered an email campaign that ticks all the boxes: messages with a PDF attached that embeds a Word document that upon opening infects the victim’s Windows PC with malware by exploiting a four-year-old code-execution vulnerability in Microsoft Office.
Booby-trapping a PDF with a malicious Word document goes against the norm of the past 10 years, according to the HP Wolf Security researchers. For a decade, miscreants have preferred Office file formats, such as Word and Excel, to deliver malicious code rather than PDFs, as users are more used to getting and opening .docx and .xlsx files. About 45 percent of malware stopped by HP’s threat intelligence team in the first quarter of the year leveraged Office formats.
“The reasons are clear: users are familiar with these file types, the applications used to open them are ubiquitous, and they are suited to social engineering lures,” Patrick Schläpfer, malware analyst at HP, explained in a write-up, adding that in this latest campaign, “the malware arrived in a PDF document – a format attackers less commonly use to infect PCs.”
While they may not be used at the same rate as Office files, cybercriminals have seen advantages in using PDFs for fraud and malware campaigns. In a 2019 report, researchers at cybersecurity firm TitanHQ found that to be effective, phishing campaigns need to create a sense of urgency or surprise as well as a sense of trust.
PDF is a document type that people trust. That’s because the public’s perception is that it is a secure document that can’t be manipulated
“This could be accomplished by spoofing your boss’s email address or by attaching some sort of business document that looks official,” they wrote. “A perfect example is a PDF document. The … PDF is a document type that people trust. That’s because the public’s perception is that it is a secure document that can’t be manipulated. After all, that’s why you issue an invoice as a PDF file and not a Word document. Unfortunately, the trust that users have in PDFs as a ‘safe’ document is false.”
They noted that in 2018, there were at least 47,000 attacks involving PDF files and that the number rose to 173,000 in the first quarter of 2019. PDFs are a threat that enterprises need to understand, Ivan Righi, senior threat intelligence analyst at Digital Shadows, told The Register.
“PDF files have capabilities similar to those of a web page,” Righi said. “They can interact with remote sites, launch local programs and contain embedded files. PDFs can also include clickable links and JavaScript, which can be exploited for malicious purposes.”
As with any phishing attempt, the cybercrook’s goal is to trick users into opening malicious documents, accepting macros in embedded files, or doing something else that will lead to malware infection, which means it’s important for organizations to ensure their employees are trained to not open documents from unknown or untrusted sources. Enterprises also can use tools like DMARC for email authentication, he said.
Old and proven
The campaign HP began tracking earlier this year aims to trick marks into running the information-stealing Snake Keylogger on their PCs, and relies on multiple techniques for evading detection, including embedding malicious files, loading remote-hosted exploits, and shellcode encryption, HP’s Schläpfer wrote.
The bad actors kick off the initial access attempt via a PDF document named “Remittance Invoice” that is attached to an email, according to HP. If the recipient opens the PDF, Adobe Reader prompts the user to open a .docx file contained within the PDF: at first glance, the dialog box that pops up appears to say the document “has been verified” and is OK to open in Microsoft Office.
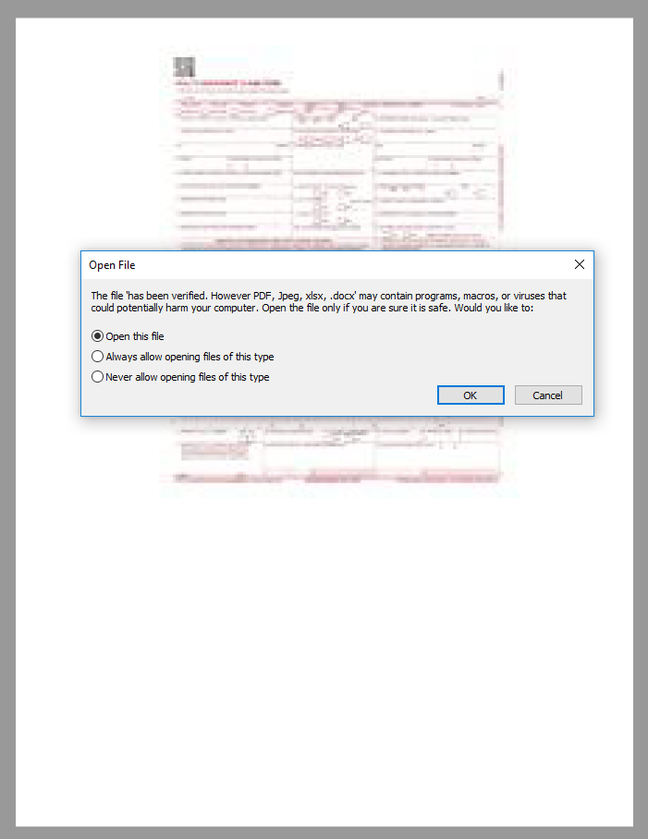
Very clever … How a carefully crafted file name for the .docx can at first glance change the meaning of a dialog box. Click to enlarge. Source: HP Wolf Spider
To pull this off and give the mark a sense that this file is legitimate, the name of the embedded .docx file is “has been verified. However PDF, Jpeg, xlsx, .docx”. When this is included in the dialog text box, it reads:
If the mark clicks on the “Open this file” option, Word opens and – if Protected View is disabled – downloads a Rich Text Format (.rtf) document named f_document_shp.doc from a web server. The file contains two badly formed OLE objects, which likely was done to evade detection and analysis. According to Schläpfer, analyzing the objects with OLE tools could return confusing results.
HP was able to use a forensic program called Foremost to reconstruct the malformed objects and view their basic information. Through this, the researchers were able to see code that exploits a code-execution vulnerability in Microsoft Equation Editor, which was fixed in November 2017 and tracked as CVE-2017-11882.
Attackers exploiting the vulnerability could run arbitrary code and take control of the PC, potentially enabling them to install programs, create new accounts with full user rights, or change or delete data. The code used to exploit the flaw was encrypted, indicating another attempt at evading detection, Schläpfer wrote.
“While Office formats remain popular, this campaign shows how attackers are also using weaponized PDF documents to infect systems,” he wrote.
“Embedding files, loading remotely-hosted exploits and encrypting shellcode are just three techniques attackers use to run malware under the radar. The exploited vulnerability in this campaign … is over four years old, yet continues being used, suggesting the exploit remains effective for attackers.”
Our takeaway from this: stay up-to-date with patches, detect and remove these PDFs from incoming messages, educate users on email safety, configure your network to contain security breaches the best you can, and other techniques that you’re more than welcome to share in the comments. ®
