Microsoft has been branded as “the world’s best malware hoster for about a decade,” thanks to abuse of the Office 365 and Live platform, as well as its slow response to reports by security researchers.
Infosec expert Kevin Beaumont, who worked at Microsoft as a senior threat intelligence analyst between June 2020 and April 2021, made the comments in response to a report by “cybersec professional” TheAnalyst.
TheAnalyst noted that a BazarLoader malware campaign was hosting its malware on Microsoft’s OneDrive service. “Does Microsoft have any responsibility in this when they KNOWINGLY are hosting hundreds of files leading to this, now for over three days?” they asked.
BazarLoader is a family of malware where a spam email attempts to trick recipients into opening a trojan via a link, in this case to an ISO (disk image that can be mounted with one click) containing a malicious DLL with a misleading shortcut called Documents that runs it, leading in time to a potential ransomware attack using Conti.
“Amusingly, while at MS we built a pipeline to alert Google Drive about Bazarloader to have the links taken down, hence why it happened so quickly (literally minutes). Now they’ve moved to Microsoft infrastructure, who have the pipeline, but can’t get Office to remove the files,” said Beaumont.
Adding to the misery, “Microsoft’s documentation specifically tells you to allowlist domains in question so security solutions don’t inspect the content. Try defending a business with a situation like this,” challenged Beaumont.
He added that “Microsoft cannot advertise themselves as the security leader with 8,000 security employees and trillions of signals if they cannot prevent their own Office365 platform being directly used to launch Conti ransomware. OneDrive abuse has been going on for years.”
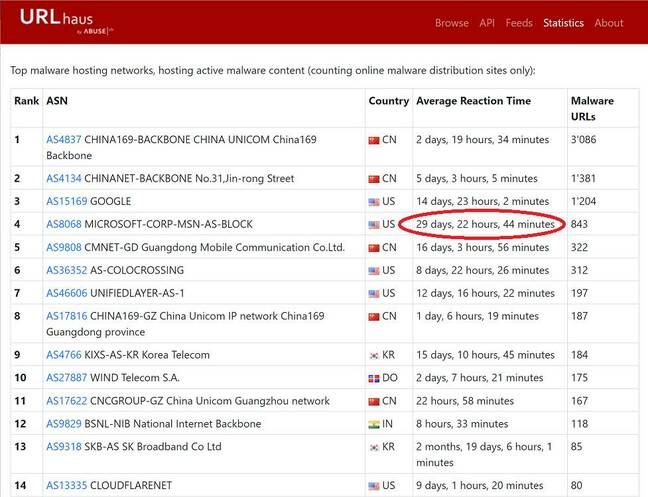
Average reaction time to malware reports: Microsoft is among the worst, and Google is also very poor
A site called URLhaus, maintained by Swiss project abuse.ch at the Bern University Institute for Cybersecurity and Engineering, keeps statistics on how long it takes for malware to be removed by the site which hosts it. The latest statistics show that Microsoft has the worst reaction time of any in the top ten sites hosting the most malware urls, at over 29 days.
According to the figures, Google hosts more malware and is also slow to remove it, but with a 14-day response time it is twice as quick as Microsoft.
The official Twitter account of abuse.ch, which runs URLhaus, said “for the record, the oldest active malware site with an age of 19 months is hosted on Sharepoint and serving GuLoader.” It added: “I’ve seen an increase of 10 new malware sites hosted at MS over the weekend. Whatever they do with these reports filled out through the MSRC API, it is definitely not automated.” MSRC is the Microsoft Security Response Center.
Beaumont said that while “My experience is the Azure Storage items should disappear very quickly … unfortunately Office is in a mess”
The Microsoft sites hosting malware use OneDrive accounts that might have been created specifically for the purpose, or hijacked from legitimate users. It is also common to see malware hosted on business Office 365 accounts that have been compromised.
Automated blocking of suspicious files by the cloud providers is problematic not only because new variants are hard to detect, but also for privacy reasons. Even if malware is detected by Microsoft Defender, it is not “automatically taken down in OneDrive,” Beaumont said.
The reaction time measures how long it takes to remove malicious content following a specific report, and is an average time to remove the malware; the full list shows that some reports take just two days and others up to 4 months.
The message for users is that seeing a link is hosted on a familiar name like OneDrive or Google Drive is not a reason to have confidence that it is safe to open – and that allow-listing those domains is a mistake.
We have asked Microsoft for comment.®