The infamous Mirai botnet was spotted by researchers who say it is spinning up again, this time with an “aggressively updated arsenal of exploits.”
It’s the first major update to the IZ1H9 Mirai variant in months and arrives bolstered with tools to break into devices from D-Link and Zyxel, among others.
Researchers at FortiGuard Labs, a team within security vendor Fortinet, said they spotted activity peaking in September, with some devices experiencing tens of thousands of attempts at break-ins every day.
“This highlights the campaign’s capacity to infect vulnerable devices and dramatically expand its botnet through the swift utilization of recently released exploit code, which encompasses numerous CVEs,” the researchers said.
The threat presented by the latest wave of Mirai activity was assigned a “critical” severity rating by FortiGuard Labs due to the scale of the attempts and the potential for remote control of the affected Linux-based devices.
Capabilities to exploit four different D-Link vulnerabilities, dated between 2015 and 2021, have been added to Mirai. All four carry near-maximum CVSS severity ratings of 9.8 and although they should ideally have been patched by now given their age, patch apathy exists across the industry and the severity of the issues highlights the threat.
Active exploitation of CVE-2016-20017, one of the four D-Link vulnerabilities Mirai can now use, was spotted by Microsoft as recently as last year in a Zerobot campaign. Successful attacks can allow attackers to remotely inject commands using a specially crafted request.
Eleven vulnerabilities, all from 2021, were also added, facilitating exploits of Sunhillo SureLine software (version 8.7.0.1.1 and earlier), Geutebruck’s video management products, and Yealink Device Management 3.6.0.20.
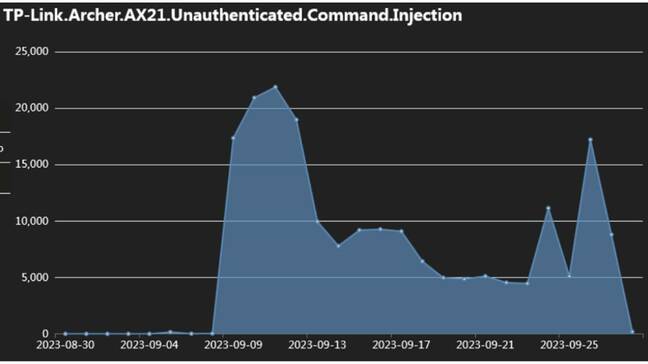
Image courtesy of Fortinet
The two most recent vulnerabilities were from 2023 and carry 8.8 CVSS severity ratings. The first, CVE-2023-1389, affects TP-Link Archer AX21 routers and CVE-2023-23295 affects the Korenix JetWave industrial wireless access point.
Twelve flaws from 2022 can now be exploited by Mirai to break into TOTOLINK routers, and researchers identified one payload with a mystery purpose.
“A similar vulnerability affects the Prolink PRC2402M router, but it is missing a few parameters to achieve remote code execution,” researchers said.
“It is unclear if the IZ1H9 campaign misused this payload or if they intended to target other devices.”
FortiGuard Labs told The Register that it was unable to determine how many of the attacks were successful – its telemetry only shows the number of attacks that generated alerts.
“Due to the nature of our telemetry, we can’t say anything about successful attacks because it would mean that our devices did not see the attack. Since we have detections for these attacks, any successful attack would need to take another route where there are no FortiGates.”
The Mirai malware showed up years ago and and first made a name for itself in 2016 after the botnet it created, referred to often as the “Mirai botnet,” was blamed for what was believed at the time to be the largest DDoS attack ever recorded.
Since then, attempts to disrupt the botnet were repeatedly made but ultimately failed. After its creators were caught by law enforcement, cybercriminals created variants of the botnet like IZ1H9, helped by Mirai’s open source code.
Over time, Mirai has evolved from targeting consumer-grade tech to Linux-based enterprise IoT devices to extend its capabilities and reach.
Despite Mirai’s longevity, since its headline-grabbing attack in 2016 it has failed to make a similarly significant impact on the cybercrime space since. ®
