Organizations looking to minimize exposure to exploitable software should scan Twitter for mentions of security bugs as well as use the Common Vulnerability Scoring System or CVSS, Kenna Security argues.
Better still is prioritizing the repair of vulnerabilities for which exploit code is available, if that information is known.
CVSS is a framework for rating the severity of software vulnerabilities (identified using CVE, or Common Vulnerability Enumeration, numbers), on a scale from 1 (least severe) to 10 (most severe). It’s overseen by First.org, a US-based, non-profit computer security organization.
As an example, the initial Log4j vulnerability (CVE-2021-4422) received a base CVSS score of 10.0. The Log4j CVSS score was also accompanied by additional data:
CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
This jumble of letters summarizes the framework version (3.0), the attack vector (network), the attack complexity (low), the privileges required (none), the user interaction required (none), whether the scope of potentially affected resources remains unchanged or not (changed), and impact metrics representing confidentiality, integrity and availability.
CVSS scores can help organizations focus on fixing dangerous flaws first. Ideally, prioritization would not be necessary but there are often so many bugs to repair that large organizations find it’s not feasible to just fix everything at once. There were more than 20,000 CVEs released last year, compared to just over 1,000 two decades ago.
While CVSS scores can inform vulnerability remediation strategies, Kenna Security, acquired last year by Cisco, argues that there are better prioritization signals like focusing on flaws with exploit code and counting the number of times a vulnerability is mentioned on Twitter.
Kenna argues for using the Exploit Prediction Scoring System (EPSS), which is also maintained by First.org.
EPSS combines CVE data with exploit data in an effort to predict whether and when vulnerabilities will be exploited.
“Prioritizing vulnerabilities with exploit code is 11 times more effective than Common Vulnerability Scoring System (CVSS) scores in minimizing exploitability,” said CTO and co-founder Ed Bellis in a blog post on Wednesday. “Mentions on Twitter, surprisingly, also have a much better signal-to-noise ratio than CVSS (about 2 times better).”
The graph below uses EPSS with remediation velocity to evaluate vulnerability repair strategies:
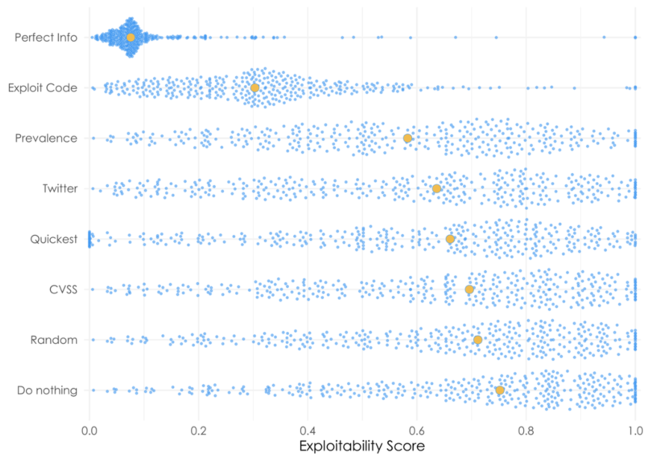
Image source: Kenna Security
Kenna Security has been working with the Cyentia Institute, a data science firm, to analyze vulnerability remediation data sets. Kenna has been publishing the findings in a series of reports, the latest of which is titled Prioritization to Prediction Volume 8, Measuring and Minimizing Exploitability.
In an email, Jay Jacobs, partner and co-founder at the Cyentia Institute, told The Register that Twitter is a better yardstick than CVSS even when a vulnerability’s CVSS score is a 10 – which makes it obvious the flaw should be dealt with.
“That metric is looking at the performance of CVSS as a whole and using it as a prioritization strategy, so it is assuming companies are remediating according to the base score,” said Jacobs. “That means they start with all of the CVSS 10s in their environment and remediate those, then move on to the next highest CVSS score and so on. They continue this until they reach their capacity for remediation as discussed in the report.”
The gist of the report is that prioritizing patches using an effective strategy can reduce an organization’s attack surface better than expanding internal capacity to apply patches.
Chris Gibson, executive director of the Forum of Incident Response and Security Teams (FIRST), told The Register in an email that CVSS and EPSS measure different things – severity and risk, respectively.
“One of the biggest challenges with CVSS has been end-user consumer education,” he said. “Many well-meaning consumers of CVSS simply stack rank vulnerabilities found in their products (CVE IDs) by CVSS Base Score and form an action/mitigation plan based on that number alone. While by far the easiest method, it’s also the least apt and accurate. Additional inputs, such as Threat and Environment, must be taken into account to come up with an accurate assessment.”
Pointing to an article on the First.org website that addresses this, he emphasized that CVSS Base Score alone is not intended to communicate the risk of malicious exploitation.
“Taken as a starting point, mitigated by real-time threat analysis such as EPSS and others, and amplified by the Security Requirements — some would call the risk tolerance — a scoring consumer can much better gauge and assess the appropriate measured response, priority, and urgency of a particular vulnerability,” he said.
The Kenna/Cyentia report also contains some noteworthy data about the exploitability of different tech vendors, based on EPSS.
It says that while Microsoft is responsible for the largest number and for the most exploitable vulnerabilities, the Windows maker manages to fix its bugs faster than almost any other vendor. When exploitability is graphed against the time that vulnerabilities linger unaddressed, HP and IBM stand out as laggards.
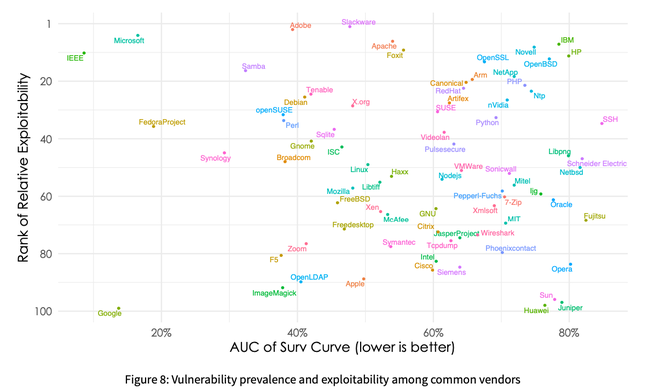
Image source: Kenna Security
Google, meanwhile, gets a nod for low exploitability and rapid repair time. “…Google is in a class of its own in terms of low exploitability and high remediation velocity,” the report says. ®
