The government of Canada has confirmed its data was accessed after two of its third-party service providers were attacked.
The third parties both provided relocation services for public sector workers and the government is currently analyzing a “significant volume of data” which could date back to 1999.
No formal conclusions have yet been made about the number of workers impacted due to the large-scale task of analyzing the relevant data.
However, the servers impacted by the breach held data related to current and former Canadian government staff, members of the Canadian armed forces, and Royal Canadian Mounted Police workers – aka Mounties.
“At this time, given the significant volume of data being assessed, we cannot yet identify specific individuals impacted; however, preliminary information indicates that breached information could belong to anyone who has used relocation services as early as 1999 and may include any personal and financial information that employees provided to the companies,” a government statement read.
It also informed the Canadian Centre for Cyber Security as well as the Office of the Privacy Commissioner and the Royal Canadian Mounted Police.
Those who think they may be affected are advised to update any login details that may be similar to those used to access BGRS or Sirva’s systems.
Enabling MFA across all accounts that are used for online transactions is also advised, as is the manual monitoring of personal accounts for any potential malicious activity.
Work is currently being carried out to identify and address any vulnerabilities that may have led to the incident, according to the statement.
“The Government of Canada is not waiting for the outcomes of this analysis and is taking a proactive, precautionary approach to support those potentially affected,” it said. “Services such as credit monitoring or reissuing valid passports that may have been compromised will be provided to current and former members of the public service, RCMP, and the Canadian Armed Forces who have relocated with BGRS or SIRVA Canada during the last 24 years.
“Additional details about the services that will be offered, and how to access them will be provided as soon as possible.”
The government of Canada first issued an alert about a September online attack on Brookfield Global Relocation Services (BGRS) on October 20. Its updated announcement on November 17 revealed intruders had accessed data from BGRS as well as Sirva, the other third-party provider.
Sirva and BGRS completed a merger in August 2022, which may explain why an attack on BGRS also meant data was impacted on Sirva’s systems.
Very little has been formally confirmed about the incident at this stage, including the scale of data scooped by the criminals, which info was compromised, how many people are affected, and how the attackers got in.
However, ransomware gang LockBit has claimed an attack on Sirva, and claimed to have published what it says is more than 1.5TB worth of documents belonging to the company, as well as three full CRM backups from its US, UK, and Australia offices. BGRS has not been named on its leak site.
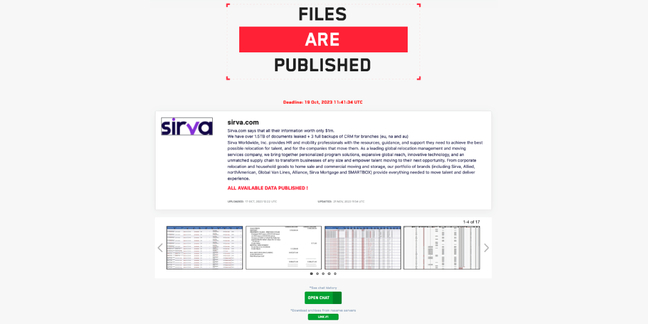
Like with the Royal Mail incident earlier this year, LockBit also published what it claims to be the entire negotiation history between its affiliate and Sirva, which spanned October 6-19 – ending the day before the government of Canada’s first breach alert.
If the messages are legitimate, the ransom was first set at $15 million but after two weeks of talks, LockBit dropped its price to a minimum of $7.5 million, in line with the criminals’ maximum 50 percent discount rule they imposed on October 1.
Sirva’s payment offer appeared to be a maximum of $1 million which was raised from an initial offer of $500,000. The general advice from authorities and experts is not to pay ransoms. Many victims never get their data back and you only have the criminal’s word for it they wont release the data – or sell it – anyway.
The Register has approached Sirva for comment but it did not reply. ®
